The CyberArk Privileged Access Security (PAS) Administration course covers CyberArk’s core PAS Solution: Enterprise Password Vault (EPV), Privileged Session Management (PSM) solutions, and Privileged Threat Analytics (PTA). CyberArk administrators, or ‘Vault Admins’, gain extensive hands-on experience in administering the core PAS Solution using our step-by-step exercise guide and dedicated lab environment.
This post is to show what kind of subjects you will learn.
CyberArk PAS Instalaltion&Configuration LAB
CyberArk PAS Basic
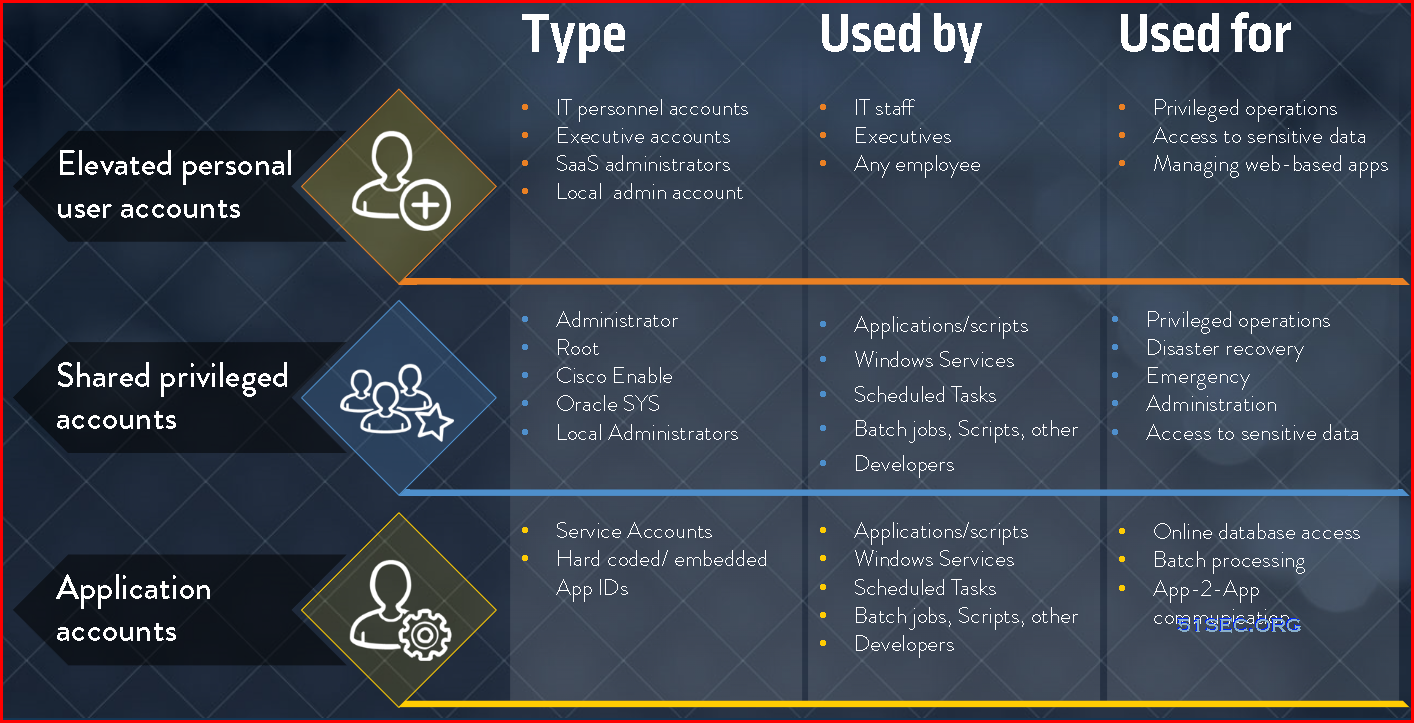
User Accounts and Identities
- Standard User Accounts
- Super Users
- Application Accounts
- Service Accounts
- Elevated personal user accounts
- Shared privileged accounts
- Application accounts
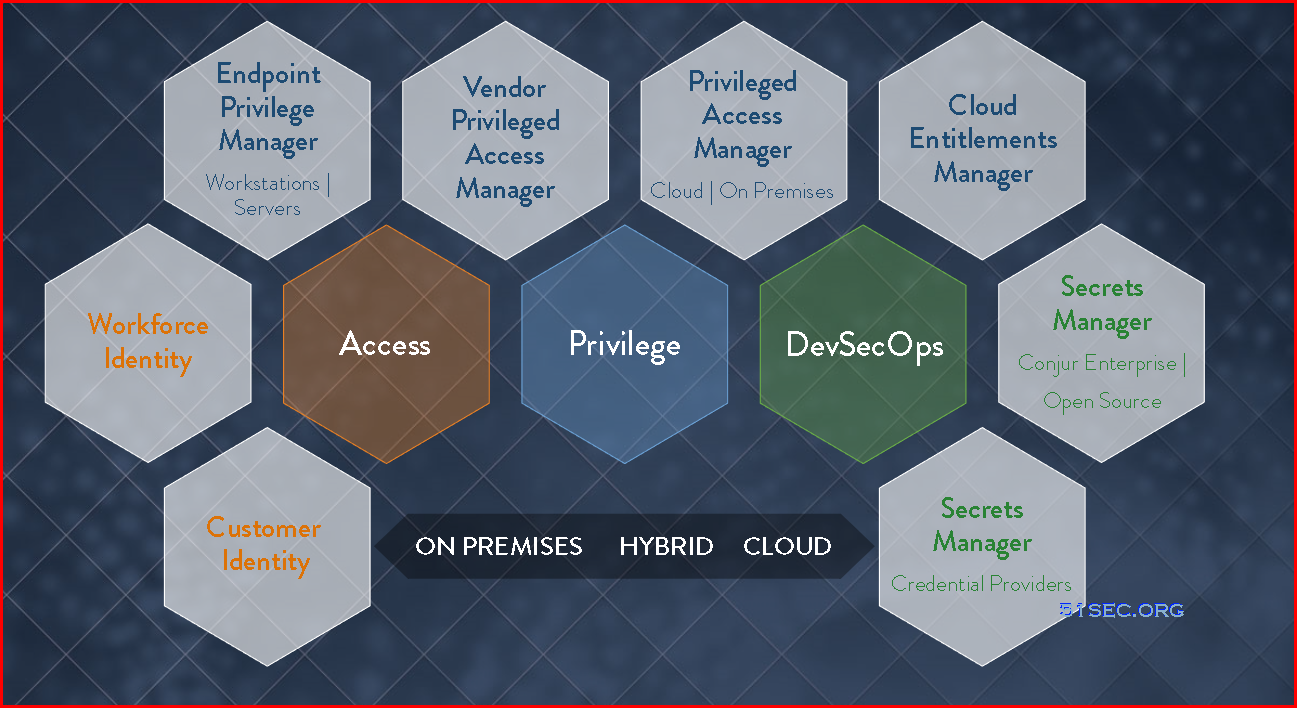
CyberArk Shared Technology Platform:
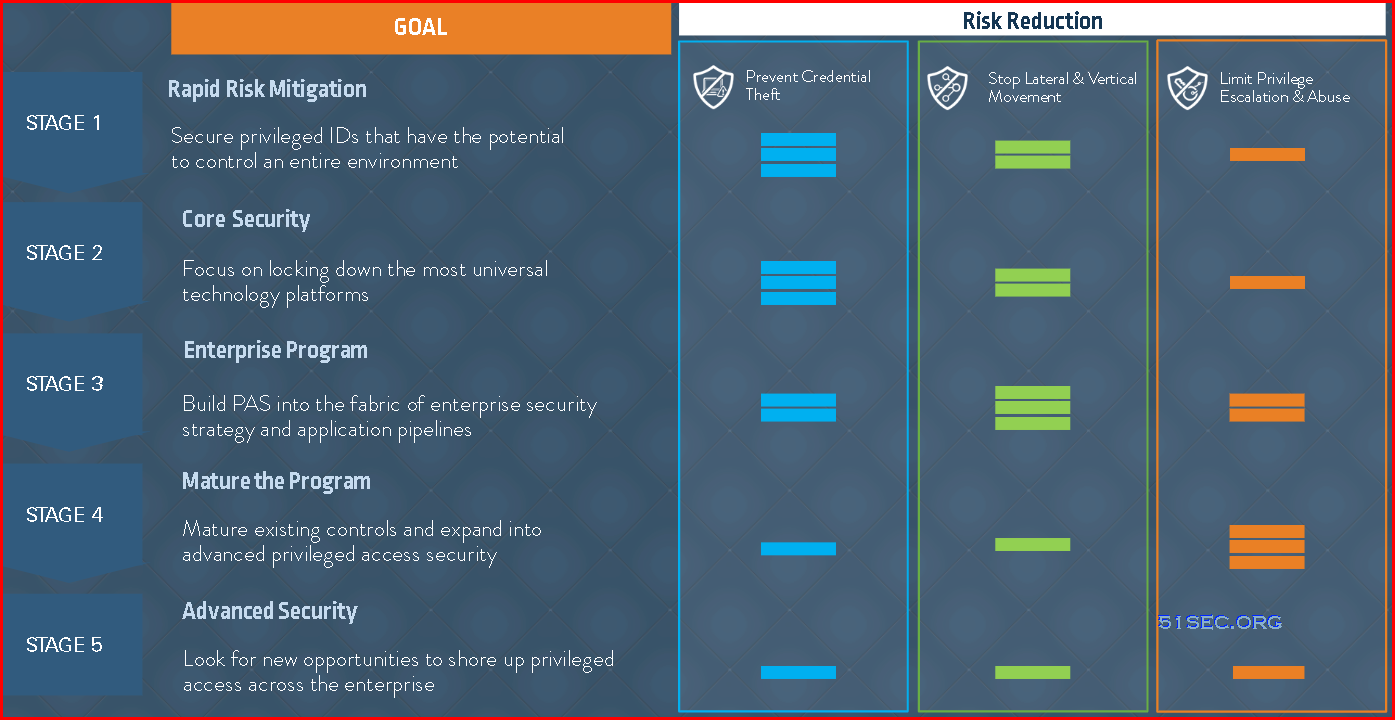
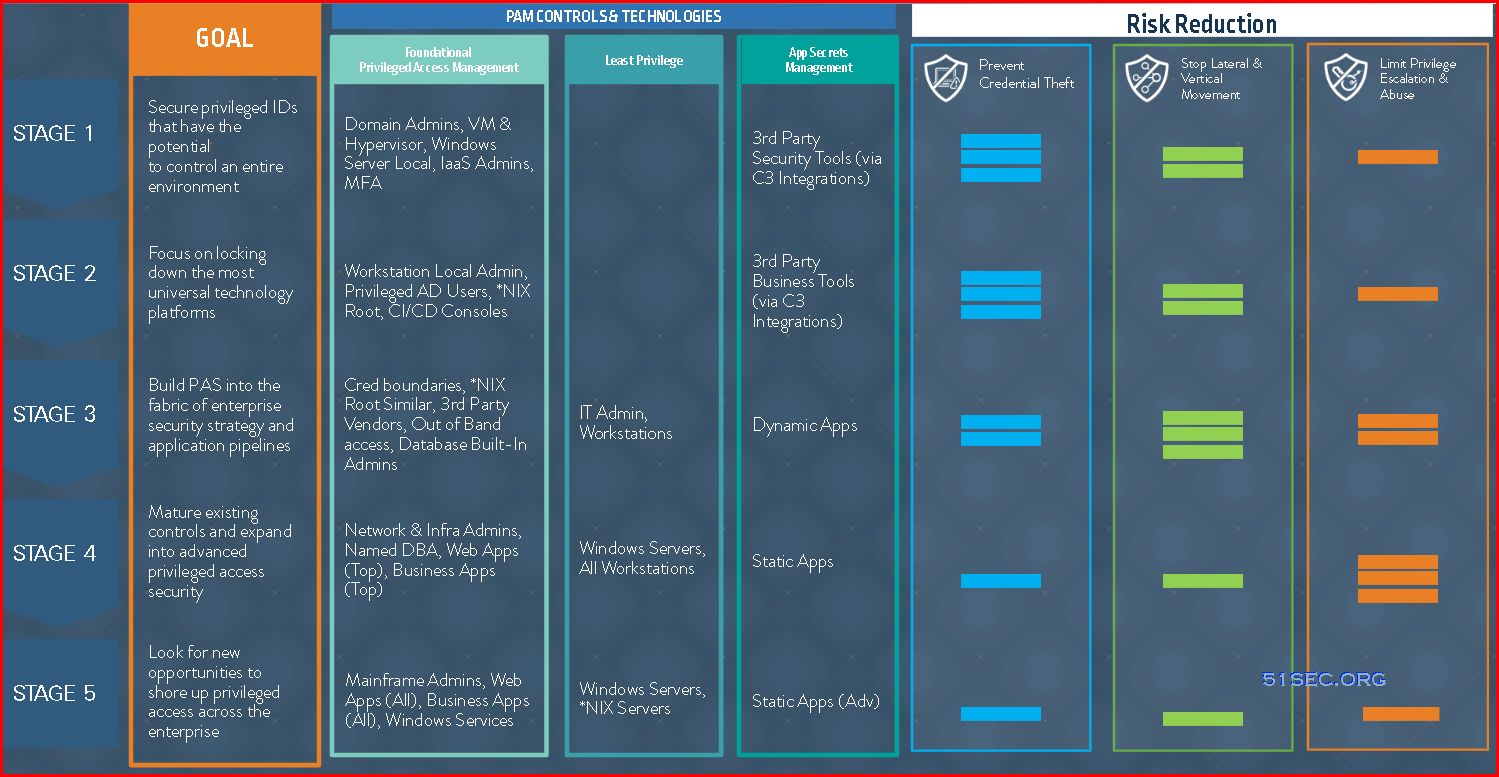
CynerArk Blueprint Stages overview
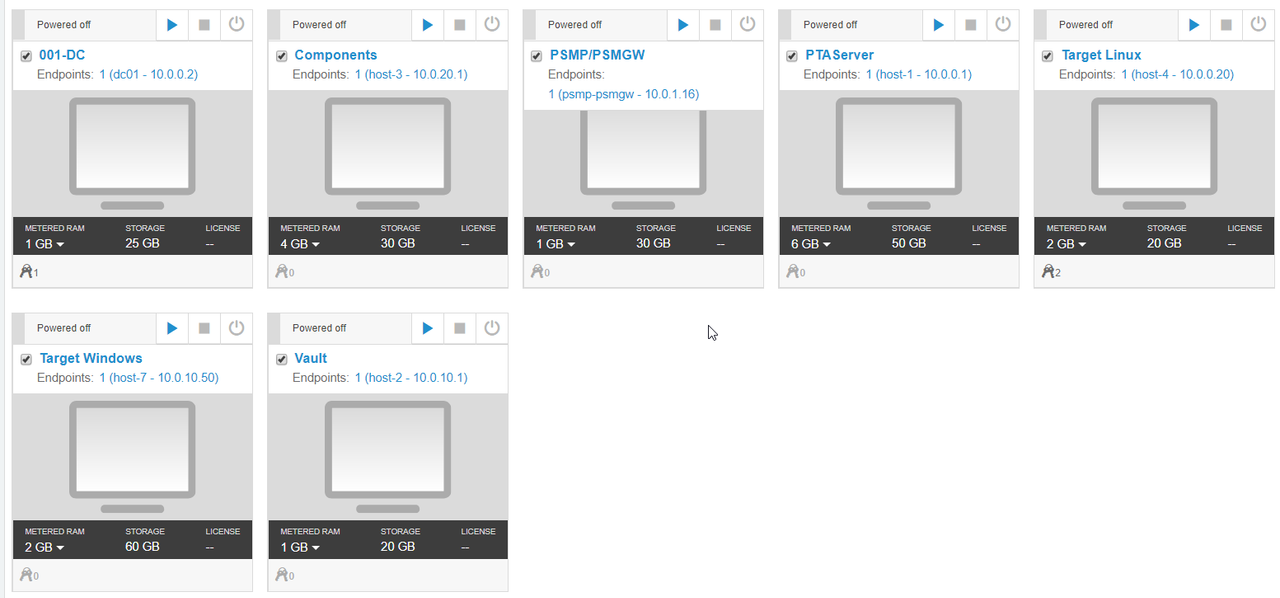
Lab Topology
For v10.10
Total Seven Machines:
001-DC: 10.0.0.2 – 1G RAM and 25G Storage
002-PVWA/PSM/CPM : 10.0.20.1 – 4G RAM and 30G Storage
003-PSMP/PSM Gateway: 10.0.1.16 – 1G RAM and 30G Storage
004-PTA : 10.0.0.1 – 6G RAM and 50G Storage
005-Target Linux: 10.0.0.20 – 2G RAM and 20G Storage
006-Target Windows: 10.0.10.50 – 2G RAM and 60G Storage
007-Vault : 10.0.10.1 – 1G RAM and 20G Storage
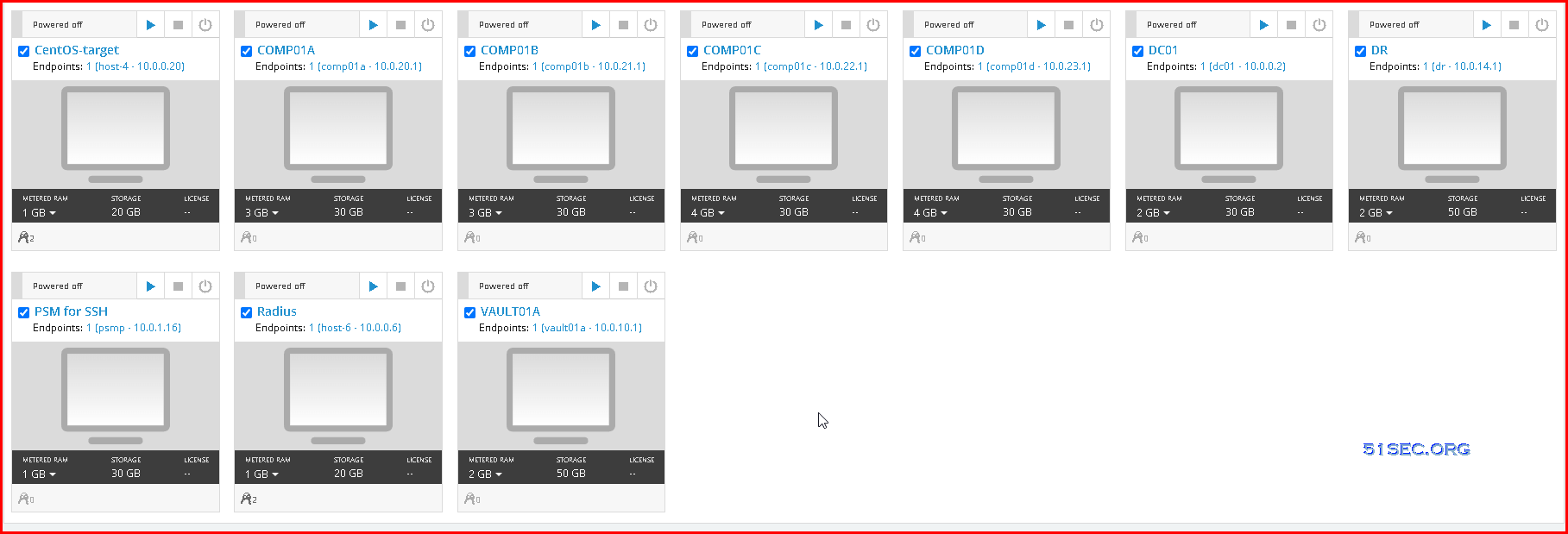
For v12.2
001-DC01: 10.0.0.1 GW 10.0.255.254 – 2G RAM, 2vCPU and 30GB Storage, Server 2019 Standard
002-Components – PVWA/PSM/CPM : 10.0.20.1 – 6G RAM, 6 vCPU and 30G Storage, Server 2019 Standard
003-psm-ssh-gw, PSMP/PSM Gateway: 10.0.30.1 – 6G RAM and 50G Storage
004-PTAserver : 10.0.30.2 – 8G RAM and 50G Storage
005-Target Win 10.0.21.1 – 2G RAM and 60G Storage, DNS 10.0.0.1, GW: 10.0.255.254
006-Target Lin: 10.0.0.20 – 1G RAM and 20G Storage
007-Vault : 10.0.10.1 – 2G RAM and 30G Storage
Lab Environment
DC01
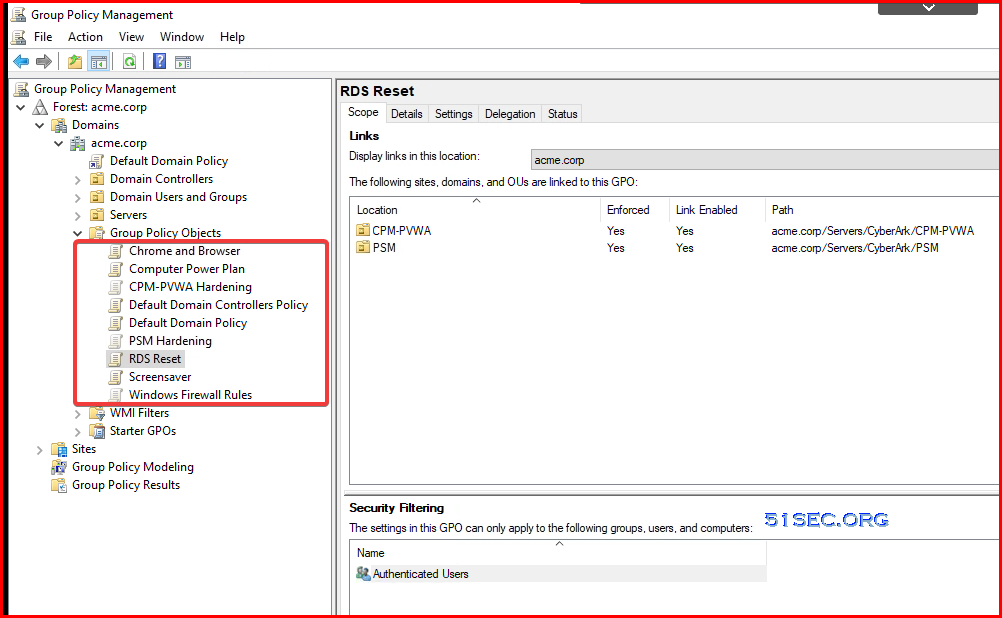
Group Policy:
Certificate Services
- https://localhost/certsrv/
Email Services
- Mailenable
Components Server – PVWA/PSM/CPM
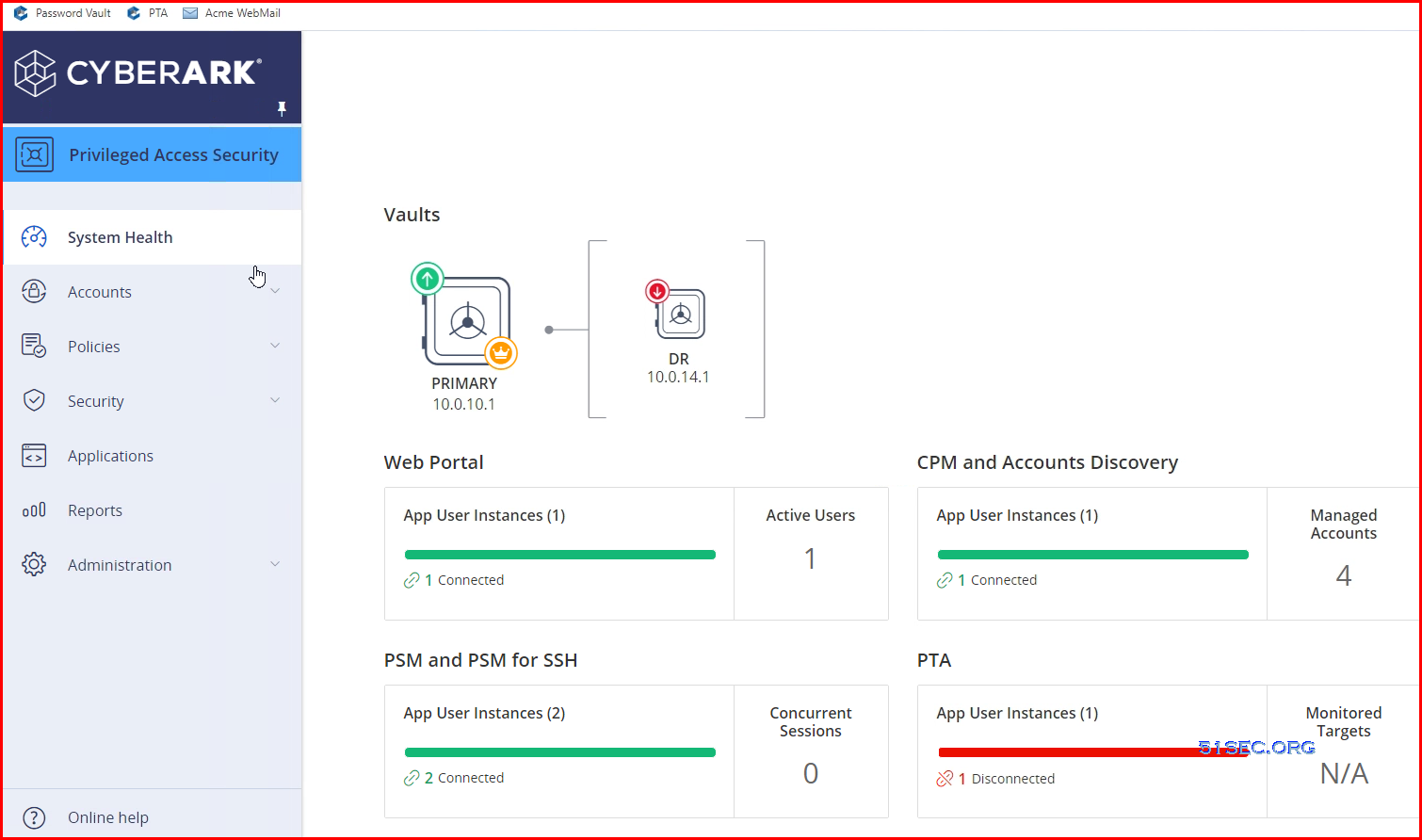
Vault Server
Vault Services
Basic Tasks for Admin (Defender)
- Vault Admin
- Auditors
- Users
- Helpdesk
- Manager
- Exception
- Activate PSM
- change password verification/reconcillation settings
- rotation days
- deactivate platform
- Create service accounts safe
- add reconcilliation accounts
- discovery scan accounts
- Win Domain
- Win local
- DB account
- Linux account
- linked account = logon account
- Linux SSH key
- Dependents – Service account
- scheduled tasks
- configuration file
- dual control
- exclusive password with automated release – check-in/check-out
- one time use
- Just-in-Time (JIT) access
- auto onboarding
- windows accounts discovery
- manual onboarding
- add accounts from file
- exception
- via HTML5 gateway
- monitoring
- recording
- detection and auto-remediation for *nix
- detection and auto-remediation for windows
Others
- Rotation CPM logs
- custom file categories
Basic Tasks for Installation and Configuration (Sentry Certification)
- Server
- Client
- Post installation
PVWA
- IIS pre-requisite using script
- import certficates
- PVWA
- Harden
- PrivateArk client
- Load Balancing
CPM
- 1st CPM
- Post Installation
- 2nd CPM
- Post Installation
- Harden
- Rename 1st CPM and update PVWA
- LDAP
- SMTP
- SIEM
- NTP
- Authentication
- Radius
- PKI
- 2FA
- Standalone PSM
- Load balanced PSM
- PSM for SSH
- Lok down user interface
- RDP over SSL
- LDAP Bind account
- PSMConnect/PSMAdminConnect
- PSM-PrivateArk Client
- PSM-PVEA-CHROME
- Vault Firewall Rules
- Master User Logging
- PSMP advanced implementation
Contents
CyberArk PAS Admin, v10.10
INTRODUCTION TO CORE PAS …………………………………………………… 14
PVWA ……………………………. 14
Log in as Administrator .. 14
Activate the PSM ………… 17
Deactivate “Reason for Access” ………………………………………………. 18
Connect using a stored account in the New UI…………………………… 18
Connect using a stored account in the Classic UI ……………………….. 20
PRIVATEARK CLIENT …………….. 23
REMOTE CONTROL CLIENT ……… 27
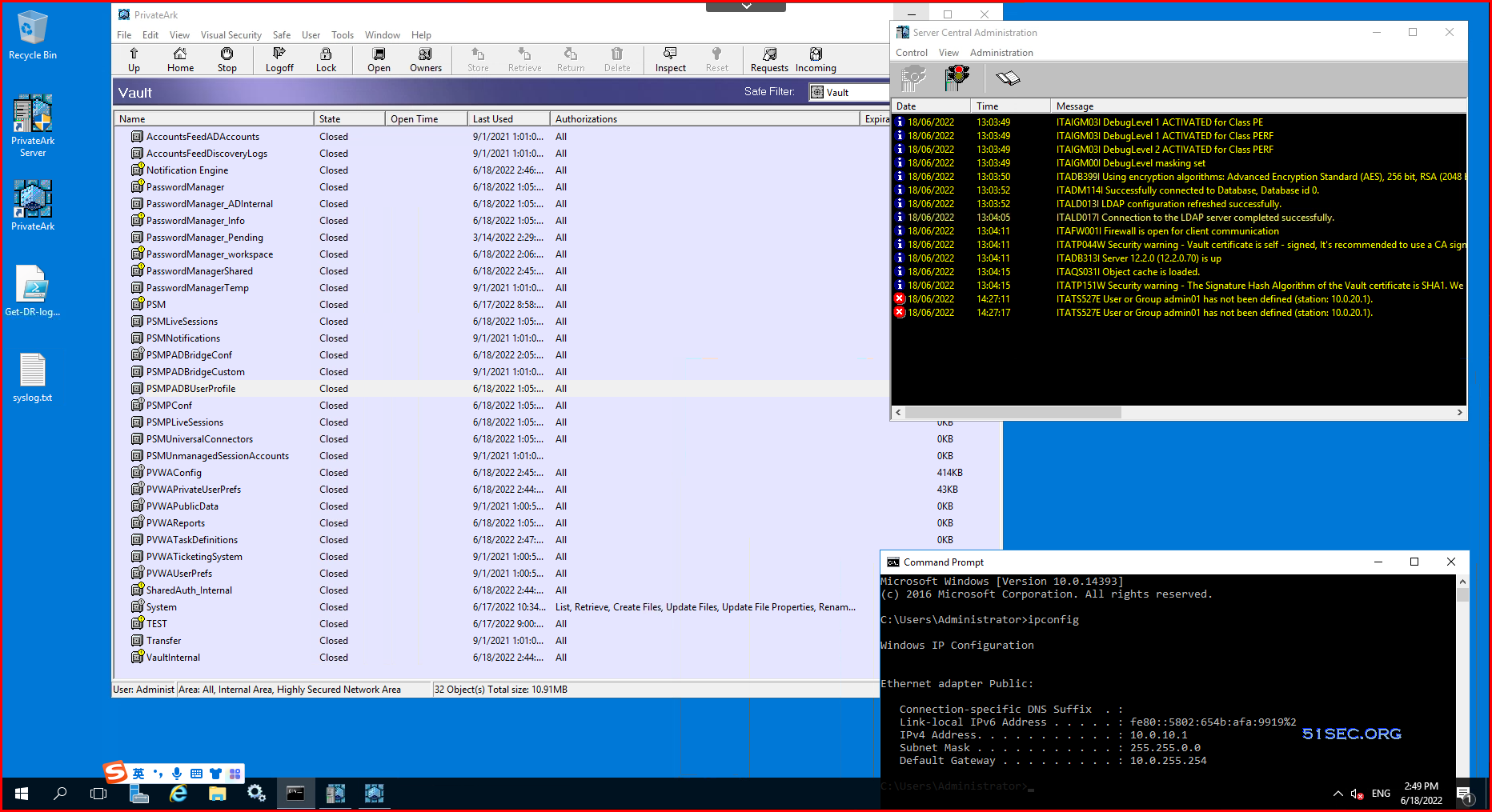
PRIVATEARK SERVER ……………. 29
USER MANAGEMENT ……. 34
Know the Players ………… 34
LDAP INTEGRATION AND DIRECTORY MAPPING ………………………………………. 35
LDAP Integration ………… 35
Configure Predefined Directory Mappings ………………………………… 39
Test the LDAP Integration and Predefined Mappings …………………. 42
Configure Custom Directory Mapping ………………………………………. 42
Test Custom Directory Mapping ………………………………………………. 45
UNSUSPEND A SUSPENDED USER (OPTIONAL) ………………………………………….. 50
LOG IN WITH MASTER …………… 53
PASSWORD MANAGEMENT – PART 1 ………………………………………… 54
SECURING WINDOWS DOMAIN ACCOUNTS …………………………………………….. 54
Platform Management … 54
Safe Management ………. 60
Account Management …. 63
EDITING THE MASTER POLICY ….. 67
Password Management . 68
SECURING UNIX SSH ACCOUNTS 72
Vault Administrator Tasks ……………………………………………… 72
Safe Manager Tasks ……. 76
Auditor Tasks ……………… 91
PASSWORD MANAGEMENT – PART 2 ………………………………………… 94
LINKED ACCOUNTS ………………. 94
Securing SSH Accounts Using a Logon account ………………………….. 94
Securing Windows Server Local Accounts via a Reconcile Account .. 97
SECURING ORACLE ACCOUNTS . 103
Vault Adminstrator Tasks ……………………………………………….. 103
Safe Manager Tasks ….. 105
SECURING AN ACCOUNT WITH SSH KEYS ……………………………………….. 107
Generating a Key-Pair .. 107
Verify You Are Able to Log in with the Private Key ……………………. 112
USAGES – SECURING SERVICE ACCOUNTS ………………………………………..116
Manage a Scheduled Task Usage …………………………………………… 116
Managing a Configuration File Usage …………………………………….. 121
PRIVILEGED ACCESS WORKFLOWS …………………………………………… 126
REQUIRE USERS TO SPECIFY REASON FOR ACCESS ………………………………… 126
Activating the Policy ….. 126
Add Predefined Reasons for Access ………………………………………… 127
REQUIRE DUAL CONTROL ACCESS APPROVAL ……………………………………… 130
Activating the Policy ….. 130
Adding an approver to a Safe …………………………………………….. 132
Testing Dual Control ….. 134
EXCLUSIVE PASSWORDS WITH AUTOMATED RELEASE AND ONE-TIME USE ………. 138
Adding a Master Policy exception for Exclusive Passwords ……….. 138
Adding a Master Policy exception for One-Time Passwords ………. 139
Reducing the Minimum Validity Period …………………………………… 140
Testing Exclusive Passwords ……………………………………………….. 141
DISCOVERY AND ONBOARDING ………………………………………………. 143
ACCOUNTS FEED ……………….. 143
Configure Automatic Onboarding Rules ………………………………….. 143
Configure and Run Windows Accounts Discovery …………………….. 145
Verify Automatically Onboarded Accounts ……………………………… 150
Manually onboard discovered accounts………………………………….. 150
PASSWORD UPLOAD UTILITY (OPTIONAL) ………………………………….. 152
Add the Administrator as a member of template safe ………………. 152
Configure and run PUU 153
PRIVILEGED SESSION MANAGEMENT ……………………………………….. 161
Disable Privileged Access Workflows ……………………………………… 161
PRIVILEGED SESSION MANAGER …………………………163
Enabling PSM …………… 163
Adding Exceptions …….. 163
Connect with a Linux Account ……………………………………………….. 165
Connect with an Oracle Account ……………………………………………. 167
Connect via HTML5 Gateway ………………………………………………… 169
Connect using PSM Ad-Hoc Connection ………………………………….. 170
PRIVILEGED SESSION MANAGER FOR WINDOWS …………………………………….. 173
PRIVILEGED SESSION MANAGER FOR SSH …………………………………………….. 176
AUDITING USER ACTIVITY IN THE PSM (MONITORING) ……………………………… 177
PSM Session Terminators ……………………………………………………… 178
Monitor, Suspend and Terminate Active Sessions …………………….. 181
Monitor Recordings …… 182
PRIVILEGED THREAT ANALYTICS ……………………………………………… 184
DETECTIONS AND AUTOMATIC REMEDIATION FOR UNIX/LINUX …………………… 184
Unmanaged Privileged Access ………………………………………………. 184
Suspected Credential Theft and Automatic Password Rotation ….. 186
Suspicious Password Change and Automatic Reconciliation ……… 189
Suspicious activities in a Unix session and automatic suspension . 191
Security Rules Exceptions ……………………………………………….. 194
DETECTIONS AND AUTOMATIC REMEDIATION FOR WINDOWS …………………….. 195
Unmanaged Privileged Access ………………………………………………. 195
Suspicious Activities in a Windows Session and Automatic Suspension …………..200
CONNECT TO THE PTA ADMINISTRATION INTERFACE ……………………………….. 203
REPORTS …………………… 205
GENERATE “PRIVILEGED ACCOUNTS INVENTORY” REPORT ………………………….. 205
GENERATE “SAFES LIST” REPORT AND “USERS LIST” REPORT ………………………. 207
GENERATE REPORTS USING EVD …………………………………………… 209
REPLICATIONS ……………. 214
BACKUP AND RESTORE ………… 214
Enabling the Backup and DR users …………………………………………. 214
Installing the PrivateArk Replicator ………………………………………… 216
Create a Safe and an Account to test Backup ………………………….. 221
Running a Backup ……… 222
Delete the Linux02 Safe 223
Running a Restore …….. 223
COMMON ADMINISTRATIVE TASKS …………………………………………. 225
ROTATING CPM LOGS ………… 225
OPTIONAL EXERCISES ….. 227
AD HOC ACCESS ……………….. 227
Set up the Ad Hoc Access Platform…………………………………………. 228
Add the Local Administrator Account …………………………………….. 230
CPM Scanner Configuration ………………………………………………….. 230
Test Ad Hoc Access ……. 231
CUSTOM FILE CATEGORIES ……. 232
Creating the Custom File Category …………………………………………. 233
Adding the Custom File Category to the Platform …………………….. 234
Making the File Categorical Searchable ………………………………….. 235
Testing the New File Category ………………………………………………. 237
CyberArk PAM Install & Configure, v10.9
INTRODUCTION…………………………………..4
USING SKYTAP………………………………………..4
INTERNATIONAL USERS………………………………… 6
SCENARIO ………………………………………….10
EPV INSTRUCTIONS………………………………..11
VAULT INSTALLATION……………………………..12
BEFORE INSTALLATION…………………………………… 12
VAULT SERVER INSTALLATION……………………………….15
PRIVATEARK CLIENT INSTALLATION………………………….23
POST VAULT INSTALLATION ……………………………… 26
INSTALL PASSWORD VAULT WEB ACCESS…………27
INSTALL IIS PRE-REQUISITE SOFTWARE USING AUTOMATIC PREREQUISITES SCRIPT ………………………………………………………… 27
REQUIRE HTTP OVER SSL (PVWA)……………………………………………………………………………………………………………. 29
INSTALL PVWA…………………………………………………………………………………………………………………………………… 29
HARDENING THE CYBERARK PVWA SERVERS …………………………………………………………………………………………………. 32
CONFIGURE IIS REDIRECTION……………………………………………………………………………………………………………………. 34
TEST PVWA LOAD BALANCING…………………………………………………………………………………………………………………. 36
INSTALL CPM (DISTRIBUTED)………………………………………………………………………………………………………………… 37
INSTALL 1
ST CPM …………………………………………………………………………………………………………………………………. 37
INSTALL THE PRIVATEARK CLIENT ON THE COMPONENT SERVER……………………………………………………………………………… 41
POST CPM INSTALLATION……………………………………………………………………………………………………………………….. 41
INSTALL 2
ND CPM…………………………………………………………………………………………………………………………………. 41
POST CPM INSTALLATION……………………………………………………………………………………………………………………….. 42
INSTALL THE PRIVATEARK CLIENT ON THE COMP01B SERVER………………………………………………………………………………… 43
RENAME 1
ST CPM………………………………………………………………………………………………………………………………… 43
UPDATE THE NAME OF THE CPM IN THE PVWA………………………………………………………………………………………………. 46
HARDEN THE CPM SERVER………………………………………………………………………………………………………………………. 46
INTEGRATIONS……………………………………………………………………………………………………………………………………. 48
LDAP AUTHENTICATION (OVER SSL)…………………………………………………………………………………………………………… 48
SMTP INTEGRATION……………………………………………………………………………………………………………………………… 53
SIEM INTEGRATION………………………………………………………………………………………………………………………………. 56
NTP INTEGRATION ……………………………………………………………………………………………………………………………….. 59
AUTHENTICATION TYPES ……………………………………………………………………………………………………………………… 62
RADIUS AUTHENTICATION ……………………………………………………………………………………………………………………… 62
PKI AUTHENTICATION ……………………………………………………………………………………………………………………………. 68
TWO FACTOR AUTHENTICATION (2FA) ………………………………………………………………………………………………………… 72
EPV TESTING AND VALIDATION…………………………………………………………………………………………………………….. 73
ADD WINDOWS DOMAIN ACCOUNT……………………………………………………………………………………………………………. 73
ADD WINDOWS SERVER LOCAL ACCOUNT……………………………………………………………………………………………………… 73
ADD LINUX ROOT ACCOUNT …………………………………………………………………………………………………………………….. 74
ADD ORACLE DATABASE ACCOUNT……………………………………………………………………………………………………………… 74
Privileged Account Security Install & Configure, v10.9
CyberArk University Exercise Guide Page 2
© Cyber-Ark® Software Ltd – No part of this material may be disclosed to any person or firm or reproduced by any means, electronic and mechanical,
without the express prior written permission of Cyber-Ark® Software Ltd.
INSTALL PSM/PSMP…………………………………………………………………………………………………………………………….. 76
INSTALL A STANDALONE PSM INSTALLATION………………………………………………………………………………………….. 77
PSM INSTALLATION PREREQUISITES ……………………………………………………………………………………………………………. 77
PSM INSTALLATION………………………………………………………………………………………………………………………………. 80
PSM POST INSTALLATION ……………………………………………………………………………………………………………………….. 83
PSM HARDENING ………………………………………………………………………………………………………………………………… 84
PSM TESTING AND VALIDATION………………………………………………………………………………………………………………… 86
LOAD BALANCED PSM SERVERS…………………………………………………………………………………………………………….. 89
CONFIGURE PSM LOAD BALANCING……………………………………………………………………………………………………………. 89
PSM FOR SSH INSTALLATION………………………………………………………………………………………………………………… 92
SECURING CYBERARK…………………………………………………………………………………………………………………………… 98
LOCK DOWN A USER’S INTERFACE………………………………………………………………………………………………………………. 98
USE RDP OVER SSL………………………………………………………………………………………………………………………………. 99
MANAGE LDAP BINDACCOUNT ………………………………………………………………………………………………………………. 104
MANAGE PSMCONNECT/PSMADMINCONNECT USING THE CPM……………………………………………………………………….. 105
MANAGE CYBERARK ADMINISTRATOR ACCOUNT USING THE CPM ……………………………………………………………………….. 109
CONNECT WITH PSM-PRIVATEARK CLIENT ………………………………………………………………………………………………….. 110
CONNECT USING PSM-PVWA-CHROME……………………………………………………………………………………………………. 113
BACKUP……………………………………………………………………………………………………………………………………………. 116
ENABLE THE BACKUP AND DR USERS …………………………………………………………………………………………………………. 116
INSTALL THE PRIVATEARK REPLICATOR COMPONENT ……………………………………………………………………………………….. 119
TESTING THE BACKUP/RESTORE PROCESS ……………………………………………………………………………………………………. 123
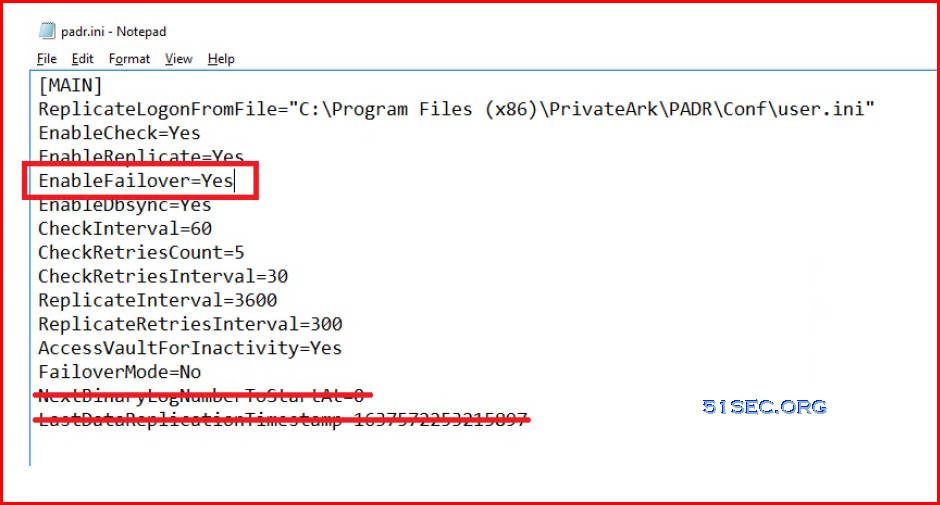
DISASTER RECOVERY………………………………………………………………………………………………………………………….. 126
INSTALL THE DISASTER RECOVERY MODULE………………………………………………………………………………………………….. 126
VALIDATE THE REPLICATION WAS SUCCESSFUL ……………………………………………………………………………………………….. 129
EXECUTE AUTOMATIC FAILOVER TEST ………………………………………………………………………………………………………… 130
EXECUTE FAILBACK PROCEDURE USING MANUAL FAILOVER ……………………………………………………………………………….. 132
(OPTIONAL) EXERCISES ………………………………………………………………………………………………………………………. 137
ADVANCED PSMP IMPLEMENTATIONS…………………………………………………………………………………………………. 138
ADDING FIREWALL RULES TO THE VAULT MANUALLY…………………………………………………………………………….. 142
References
- https://training.cyberark.com/
- https://cyberark.influitive.com/
- https://champions.cyberark.com/
- https://cyberark-customers.force.com/s/


Hi johnyan,
Could you please share the link for Contents?
Thanks,
Bhagya