Starting to collect some PowerShell and CMD commands and scripts for future references. There are lots of them can be found from the references section.
This post will be constantly updated once I found there is any other interesting and usful script.
Table of Contents
Test remote port if open – Test-NetConnection
PS C:\Users\test1> Test-NetConnection ComputerName : internetbeacon.msedge.net
RemoteAddress : 13.107.4.52
InterfaceAlias : Ethernet0
SourceAddress : 192.168.2.141
PingSucceeded : True
PingReplyDetails (RTT) : 14 ms
PS C:\Users\test1>
PS C:\Users\test1> Test-NetConnection -ComputerName fileshare2cool.file.core.windows.net -Port 445
WARNING: TCP connect to (52.239.170.104 : 445) failed
WARNING: Ping to 52.239.170.104 failed with status: TimedOut
ComputerName : fileshare2cool.file.core.windows.net
RemoteAddress : 52.239.170.104
RemotePort : 445
InterfaceAlias : Ethernet0
SourceAddress : 192.168.2.141
PingSucceeded : False
PingReplyDetails (RTT) : 0 ms
TcpTestSucceeded : False
Test-NetConnection cmdlet. To use the Test-NetConnection cmdlet, the Azure PowerShell module must be installed, see Install Azure PowerShell module for more information. Remember to replace <your-storage-account-name> and <your-resource-group-name> with the relevant names for your storage account.$resourceGroupName = "<your-resource-group-name>"
$storageAccountName = "<your-storage-account-name>"
# This command requires you to be logged into your Azure account, run Login-AzAccount if you haven't
# already logged in.
$storageAccount = Get-AzStorageAccount -ResourceGroupName $resourceGroupName -Name $storageAccountName
# The ComputerName, or host, is <storage-account>.file.core.windows.net for Azure Public Regions.
# $storageAccount.Context.FileEndpoint is used because non-Public Azure regions, such as sovereign clouds
# or Azure Stack deployments, will have different hosts for Azure file shares (and other storage resources).
Test-NetConnection -ComputerName ([System.Uri]::new($storageAccount.Context.FileEndPoint).Host) -Port 445
Get DNS Name Resolution Policy Table (NRPT) Details
PS C:\Users\jon> Get-DnsClientNrptPolicy
Namespace : .file.core.windows.net
QueryPolicy :
SecureNameQueryFallback :
DirectAccessIPsecCARestriction :
DirectAccessProxyName :
DirectAccessDnsServers :
DirectAccessEnabled :
DirectAccessProxyType : NoProxy
DirectAccessQueryIPsecEncryption :
DirectAccessQueryIPsecRequired : False
NameServers : {10.3.0.19, 10.5.99.19}
DnsSecIPsecCARestriction :
DnsSecQueryIPsecEncryption :
DnsSecQueryIPsecRequired : False
DnsSecValidationRequired : False
NameEncoding : Utf8WithoutMapping
Namespace : .corp.51sec.com
QueryPolicy :
SecureNameQueryFallback :
DirectAccessIPsecCARestriction :
DirectAccessProxyName :
DirectAccessDnsServers :
DirectAccessEnabled :
DirectAccessProxyType : NoProxy
DirectAccessQueryIPsecEncryption :
DirectAccessQueryIPsecRequired : False
NameServers : {10.3.0.19, 10.5.99.19}
DnsSecIPsecCARestriction :
DnsSecQueryIPsecEncryption :
DnsSecQueryIPsecRequired : False
DnsSecValidationRequired : False
NameEncoding : Utf8WithoutMapping
Namespace : https://azuregateway-db380066-8803-43f0-ba5a-1111-22222222fad333.vpn.azure.com
QueryPolicy :
SecureNameQueryFallback :
DirectAccessIPsecCARestriction :
DirectAccessProxyName :
DirectAccessDnsServers :
DirectAccessEnabled :
DirectAccessProxyType : NoProxy
DirectAccessQueryIPsecEncryption :
DirectAccessQueryIPsecRequired : False
NameServers :
DnsSecIPsecCARestriction :
DnsSecQueryIPsecEncryption :
DnsSecQueryIPsecRequired : False
DnsSecValidationRequired : False
NameEncoding : Utf8WithoutMapping
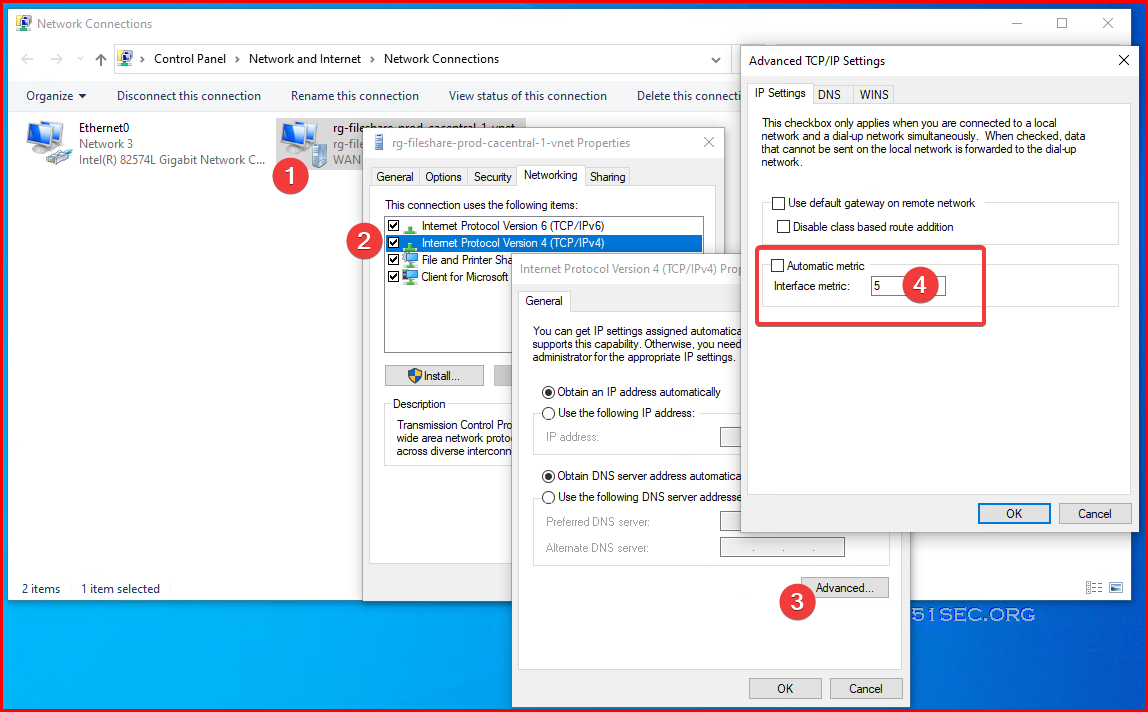
Check and Change Interface Metric Value
C:\Users\netsec>netsh interface ipv4 show interface
Idx Met MTU State Name
--- ---------- ---------- ------------ ---------------------------
24 55 1400 connected rg-fs-prod-ca-1-vnet
1 75 4294967295 connected Loopback Pseudo-Interface 1
14 25 1500 connected Ethernet0
C:\Users\netsec>netsh interface ipv4 show interface Idx Met MTU State Name --- ---------- ---------- ------------ --------------------------- 24 5 1400 connected rg-fileshare-prod-cacentral-1-vnet 1 75 4294967295 connected Loopback Pseudo-Interface 1 14 25 1500 connected Ethernet0
- netsh interface ipv4 set interface “Local Area Connection” metric=5
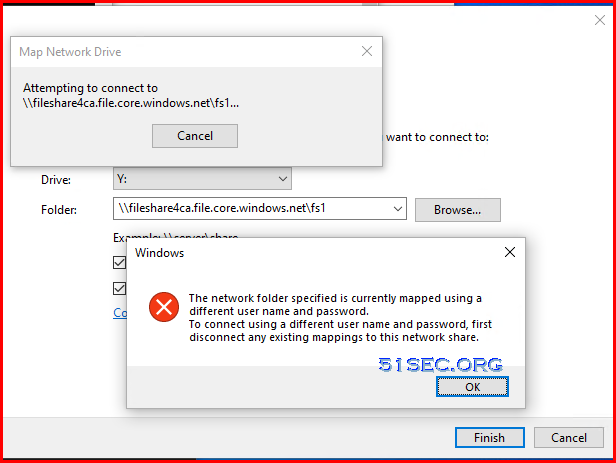
Check Mapped Network Shares
New connections will not be remembered.
Status Local Remote Network
——————————————————————————-
OK J: \\192.168.2.13\Jobs Microsoft Windows Network
OK K: \\192.168.2.13\Database Microsoft Windows Network
Disconnected O: \\fileshareca.file.core.windows.net\fs1
Microsoft Windows Network
OK P: \\192.168.2.13\Personal Microsoft Windows Network
OK S: \\192.168.2.13\Software Microsoft Windows Network
OK V: \\192.168.2.13\51sec Microsoft Windows Network
OK X: \\192.168.2.13\ArchiveView Microsoft Windows Network
OK Z: \\192.168.2.82\Measurement Data
Microsoft Windows Network
The command completed successfully.
C:\Users\jon>net use O: /delete
O: was deleted successfully.
C:\Users\jon>net use
New connections will not be remembered.
Status Local Remote Network
——————————————————————————-
OK J: \\192.168.2.13\Jobs Microsoft Windows Network
OK K: \\192.168.2.13\Database Microsoft Windows Network
OK P: \\192.168.2.13\Personal Microsoft Windows Network
OK S: \\192.168.2.13\Software Microsoft Windows Network
OK V: \\192.168.2.13\51sec Microsoft Windows Network
OK X: \\192.168.2.13\ArchiveView Microsoft Windows Network
OK Z: \\192.168.2.82\Measurement Data
Microsoft Windows Network
The command completed successfully.
C:\Users\jon>
Access Network Drive in PowerShell
I’m running PowerShell in a Windows 7 x64 virtual machine. I have a shared folder on the host mapped as a network drive (Z:). When I run PS normally I can access that drive just fine, but if I run it “as administrator” it tells me:
Set-Location : Cannot find drive. A drive with the name 'Z' does not exist.
At line:1 char:13
+ Set-Location <<<< Z:
+ CategoryInfo : ObjectNotFound: (Z:String) [Set-Location], DriveNotFoundException
+ FullyQualifiedErrorId : DriveNotFound,Microsoft.PowerShell.Commands.SetLocationCommandIn the end the fix was simply to re-map the drive letter while running as Administrator:
net use Z: "\\vmware-host\Shared Folders"
note: Map to an available drive: net use * \\quic.51sec.org\temp
Export a Computer List from Active Directory
Open the Powershell ISE → Run the following script, adjusting the path for the export:
Get-ADComputer -Filter * -Property * | Select-Object Name,OperatingSystem,OperatingSystemVersion,ipv4Address | Export-CSV ADcomputerslist.csv -NoTypeInformation -Encoding UTF8
Get-Aduser -Filter * -Properties *|select EmailAddress,name,SamAccountName,GivenName,SurName,@{n='Manager';e={(Get-aduser $_.manager).name}},Title,Enabled,Description,Department,LastLogonDate|export-csv "C:\temp\all_users.csv"
List disabled users
For example, let’s display the list of disabled user accounts in domain:
Search-ADAccount -UsersOnly –AccountDisabled
You can limit the search scope to a specific Active Directory container (OU):
Search-ADAccount -UsersOnly –AccountDisabled –searchbase "OU=Admins,OU=Accounts,DC=woshub,DC=com"
If you need to get the list of the disabled users containing certain user attributes and present it as a graphic table to be sorted, run the following:
Search-ADAccount -UsersOnly AccountDisabled |sort LastLogonDate | Select Name,LastLogonDate,DistinguishedName |out-gridview -title "Disabled Users"
Bulk Create AD Users From CSV with PowerShell
Note: https://www.alitajran.com/create-active-directory-users-from-csv-with-powershell/
FirstName;Initials;Lastname;Username;Email;StreetAddress;City;ZipCode;State;Country;Department;Password;Telephone;JobTitle;Company;OU
admin1;a1;admin1;admin1;[email protected];21 Baker St;London;NW1 6XE;;CA;IT;Cyberark1;;Engineer;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
admin2;a2;admin2;admin2;[email protected];21 Baker St;London;NW1 6XE;;CA;IT;Cyberark1;;Engineer;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
vaultadmin1;va1;vaultadmin1;vaultadmin1;[email protected];21 Baker St;London;NW1 6XE;;CA;IT;Cyberark1;;Engineer;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
vaultadmin2;va2;vaultadmin2;vaultadmin2;[email protected];21 Baker St;London;NW1 6XE;;CA;IT;Cyberark1;;Engineer;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
auditor1;au1;auditor1;auditor1;[email protected];21 Baker St;London;NW1 6XE;;CA;IT;Cyberark1;;Engineer;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
auditor2;au2;auditor2;auditor2;[email protected];21 Baker St;London;NW1 6XE;;CA;IT;Cyberark1;;Engineer;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
test1;t1;test1;test1;[email protected];21 Baker St;London;NW1 6XE;;GB;IT;Cyberark1;+44123456781;Manager;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
test2;t2;test2;test2;[email protected];21 Baker St;London;NW1 6XE;;GB;IT;Cyberark1;+44123456782;Engineer;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
manager1;m1;manager1;manager1;[email protected];21 Baker St;London;NW1 6XE;;GB;IT;Cyberark1;+44123456783;Teamleader;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
manager2;m2;manager2;manager2;[email protected];21 Baker St;London;NW1 6XE;;GB;IT;Cyberark1;+44123456783;Teamleader;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
support1;s1;support1;support1;[email protected];21 Baker St;London;NW1 6XE;;GB;IT;Cyberark1;+44123456783;Teamleader;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
support2;s2;support2;support2;[email protected];21 Baker St;London;NW1 6XE;;GB;IT;Cyberark1;+44123456783;Teamleader;51sec;OU=IT,OU=Users,OU=Test,DC=51sec,DC=corp
Import-Module ActiveDirectory
# Store the data from NewUsersFinal.csv in the $ADUsers variable
$ADUsers = Import-Csv C:\temp\NewUsersFinal.csv -Delimiter “;”
# Define UPN
$UPN = “51sec.corp”
# Loop through each row containing user details in the CSV file
foreach ($User in $ADUsers) {
#Read user data from each field in each row and assign the data to a variable as below
$username = $User.username
$password = $User.password
$firstname = $User.firstname
$lastname = $User.lastname
$initials = $User.initials
$OU = $User.ou #This field refers to the OU the user account is to be created in
$email = $User.email
$streetaddress = $User.streetaddress
$city = $User.city
$zipcode = $User.zipcode
$state = $User.state
$country = $User.country
$telephone = $User.telephone
$jobtitle = $User.jobtitle
$company = $User.company
$department = $User.department
# Check to see if the user already exists in AD
if (Get-ADUser -F { SamAccountName -eq $username }) {
# If user does exist, give a warning
Write-Warning “A user account with username $username already exists in Active Directory.”
}
else {
# User does not exist then proceed to create the new user account
# Account will be created in the OU provided by the $OU variable read from the CSV file
New-ADUser `
-SamAccountName $username `
-UserPrincipalName “$username@$UPN” `
-Name “$firstname $lastname” `
-GivenName $firstname `
-Surname $lastname `
-Initials $initials `
-Enabled $True `
-DisplayName “$lastname, $firstname” `
-Path $OU `
-City $city `
-PostalCode $zipcode `
-Country $country `
-Company $company `
-State $state `
-StreetAddress $streetaddress `
-OfficePhone $telephone `
-EmailAddress $email `
-Title $jobtitle `
-Department $department `
-AccountPassword (ConvertTo-secureString $password -AsPlainText -Force) -ChangePasswordAtLogon $True
# If user is created, show message.
Write-Host “The user account $username is created.” -ForegroundColor Cyan
}
}
Read-Host -Prompt “Press Enter to exit”
Reset Domain User’s Password
1. Using Powershell
Set-ADAccountPassword -Identity admin2 -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Cyberark1!" -Force)
Set-ADAccountPassword -Identity auditor1 -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Cyberark1!" -Force)
Set-ADAccountPassword -Identity auditor2 -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Cyberark1!" -Force)
Set-ADAccountPassword -Identity test1 -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Cyberark1!" -Force)
Set-ADAccountPassword -Identity test2 -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Cyberark1!" -Force)
Set-ADAccountPassword -Identity vaultadmin1 -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Cyberark1!" -Force)
Set-ADAccountPassword -Identity vaultadmin2 -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Cyberark1!" -Force)
2. Use Command Prompt
net user /domain USERNAME NEWPASS.
Run command prompt as administrator:
C:\Windows\system32>net user /domain admin2 Cyberark1!
The command completed successfully.
For Exchange Online Management
PS C:\Windows\system32> Install-Module -Name ExchangeOnlineManagement -RequiredVersion 2.0.5 NuGet provider is required to continue
PowerShellGet requires NuGet provider version '2.8.5.201' or newer to interact with NuGet-based repositories. The NuGet
provider must be available in 'C:\Program Files\PackageManagement\ProviderAssemblies' or
'C:\Users\xxyan\AppData\Local\PackageManagement\ProviderAssemblies'. You can also install the NuGet provider by running
'Install-PackageProvider -Name NuGet -MinimumVersion 2.8.5.201 -Force'. Do you want PowerShellGet to install and
import the NuGet provider now?
[Y] Yes [N] No [S] Suspend [?] Help (default is "Y"):
Untrusted repository
You are installing the modules from an untrusted repository. If you trust this repository, change its
InstallationPolicy value by running the Set-PSRepository cmdlet. Are you sure you want to install the modules from
'PSGallery'?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "N"): Y
PS C:\Windows\system32> Set-ExecutionPolicy RemoteSigned
Execution Policy Change
The execution policy helps protect you from scripts that you do not trust. Changing the execution policy might expose
you to the security risks described in the about_Execution_Policies help topic at
https:/go.microsoft.com/fwlink/?LinkID=135170. Do you want to change the execution policy?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "N"): A
PS C:\Windows\system32>
Clear Cached Credentials
Clear cached credentials (NetID+password) in Windows 10?
- Open the start menu, in the search bar type: control panel
- You will see an application called control panel, select this item.
- In the control panel window, open the Credential Manager control panel.
- In the Credential Manager control panel, click on Windows Credentials.
- From there you can check/edit/delete your saved network credentials.
Clear cached credentials (NetID+password) in Windows 7?
If a mapped drive (not recommended): From Windows Explorer -> Tools -> Disconnect Network Drive
If not a mapped drive, from command prompt (run as administrator):
rundll32.exe keymgr.dll, KRShowKeyMgr
Then select any network share to clear credentials for, then click delete button. (no network shares listed).
You can also edit the credentials if you just need to fix a mistake.
Disable Unneeded / Unnecessary Services
For Windows 10 / 11
$serviceList = @”
AppVClient
debugregsvc
iphlpsvc
MapsBroker
NetTcpPortSharing
RemoteAccess
RemoteRegistry
SCardSvr
shpamsvc
SysMain
tzautoupdate
UevAgentService
WebManagement
“@
$serviceList = $serviceList.Split(“`n”)
foreach($service in $serviceList)
{
Get-Service -name $service -ErrorAction SilentlyContinue | Stop-Service -ErrorAction SilentlyContinue
Get-Service -name $service -ErrorAction SilentlyContinue | Set-Service -StartupType Disabled -ErrorAction SilentlyContinue
}
For Windows Server 2019 / 2022:
Windows Registry Editor Version 5.00
;Disabling various services which have no real use on Windows Server as per Microsoft document here
;https://docs.microsoft.com/en-us/windows-server/security/windows-services/security-guidelines-for-disabling-system-services-in-windows-server
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CDPUserSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WpnService]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\bthserv]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\OneSyncSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PimIndexMaintenanceSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UserDataSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UnistoreSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WpnUserService]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WpnUserService]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\xboxgip]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\dmwappushservice]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\icssvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lfsvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MapsBroker]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NcbService]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NgcSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PhoneSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RmSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SensrSvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SensorDataService]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SensorService]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ShellHWDetection]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\TabletInputService]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WalletService]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wisvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wlidsvc]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\XblAuthManager]
“Start”=dword:00000004
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\XblGameSave]
“Start”=dword:00000004
Create a File of Specific Size
fsutil file createnew c:\data\winaero.bin 4096
Common CMD Commands
1. gpedit.msc—–组策略
2. sndrec32——-录音机
3. Nslookup——-IP地址侦测器 ,是一个 监测网络中 DNS 服务器是否能正确实现域名解析的命令行工具。
4. explorer——-打开资源管理器
5. logoff———注销命令
6. shutdown——-60秒倒计时关机命令. Launch a Remote Shutdown GUI: shutdown -i
7. lusrmgr.msc—-本机用户和组
8. services.msc—本地服务设置
9. oobe/msoobe /a—-检查XP是否激活
10. notepad——–打开记事本
11. cleanmgr——-垃圾整理
12. net start messenger—-开始信使服务
13. compmgmt.msc—计算机管理
14. net stop messenger—–停止信使服务
15. conf———–启动netmeeting
16. dvdplay——–DVD播放器
17. charmap——–启动字符映射表
18. diskmgmt.msc—磁盘管理实用程序
19. calc———–启动计算器
20. dfrg.msc——-磁盘碎片整理程序
21. chkdsk.exe—–Chkdsk磁盘检查
22. devmgmt.msc— 设备管理器
23. regsvr32 /u *.dll—-停止dll文件运行
24. drwtsn32—— 系统医生
25. rononce -p—-15秒关机
26. dxdiag———检查DirectX信息
27. regedt32——-注册表编辑器
28. Msconfig.exe—系统配置实用程序
29. rsop.msc——-组策略结果集
30. mem.exe——–显示内存使用情况
31. regedit.exe—-注册表
32. winchat——–XP自带局域网聊天
33. progman——–程序管理器
34. winmsd———系统信息
35. perfmon.msc—-计算机性能监测程序
36. winver———检查Windows版本
37. sfc /scannow—–扫描错误并复原
38. taskmgr—–任务管理器(2000/xp/2003
40. wmimgmt.msc—-打开windows管理体系结构(WMI)
41. wupdmgr——–windows更新程序
42. wscript——–windows脚本宿主设置
43. write———-写字板
45. wiaacmgr——-扫描仪和照相机向导
46. winchat——–XP自带局域网聊天
49. mplayer2——-简易widnows media player
50. mspaint——–画图板
51. mstsc———-远程桌面连接
53. magnify——–放大镜实用程序
54. mmc————打开控制台
55. mobsync——–同步命令
57. iexpress——-木马捆绑工具,系统自带
58. fsmgmt.msc—–共享文件夹管理器
59. utilman——–辅助工具管理器
61. dcomcnfg——-打开系统组件服务
62. ddeshare——-打开DDE共享设置
110. osk————打开屏幕键盘
111. odbcad32——-ODBC数据源管理器
112. oobe/msoobe /a—-检查XP是否激活
68. ntbackup——-系统备份和还原
69. narrator——-屏幕“讲述人”
70. ntmsmgr.msc—-移动存储管理器
71. ntmsoprq.msc—移动存储管理员操作请求
72. netstat -an—-(TC)命令检查接口
73. syncapp——–创建一个公文包
74. sysedit——–系统配置编辑器
75. sigverif——-文件签名验证程序
76. ciadv.msc——索引服务程序
77. shrpubw——–创建共享文件夹
78. secpol.msc—–本地安全策略
79. syskey———系统加密,一旦加密就不能解开,保护windows xp系统的双重密码
80. services.msc—本地服务设置
81. Sndvol32——-音量控制程序
82. sfc.exe——–系统文件检查器
83. sfc /scannow—windows文件保护
84. ciadv.msc——索引服务程序
85. tourstart——xp简介(安装完成后出现的漫游xp程序)
86. taskmgr——–任务管理器
87. eventvwr——-事件查看器
88. eudcedit——-造字程序
89. compmgmt.msc—计算机管理
90. packager——-对象包装程序
91. perfmon.msc—-计算机性能监测程序
92. charmap——–启动字符映射表
93. cliconfg——-SQL SERVER 客户端网络实用程序
94. Clipbrd——–剪贴板查看器
95. conf———–启动netmeeting
96. certmgr.msc—-证书管理实用程序
97. regsvr32 /u *.dll—-停止dll文件运行
98. regsvr32 /u zipfldr.dll——取消ZIP支持
References
- /u/jacfearsome https://github.com/JacFearsome/powershell-scripts
- /u/PowerMonkey500 https://github.com/AndrewEllis93/PowerShell-Scripts
- /u/unibody https://github.com/jwmoss/powershell_scripts
- /u/IDA_noob https://github.com/tylerapplebaum?tab=repositories
- /u/mikedopp https://github.com/mikedopp
- /u/JBear_Alpha https://github.com/Average-Bear
- /u/BornToBeRoot https://github.com/BornToBeRoot/PowerShell
- /u/ramblingcookiemonste https://github.com/RamblingCookieMonster/PowerShell
- /u/jhulbe https://github.com/jhulbe/Powershell
- jrussellfreelance/powershell-scripts