While governance includes oversight, it is a broader concept. Governance refers to the structures, systems, and practices an organization has in place to:
- assign decision-making authorities, define how decisions are to be made, and establish the organization’s strategic direction;
- oversee the delivery of its services; the implementation of its policies, plans, programs, and projects; and the monitoring and mitigation of its key risks; and
- report on its performance in achieving intended results and use performance information to drive ongoing improvements and corrective actions.
A simplified governance framework is presented in Figure 1.
Figure 1
A Simplified Governance Framework
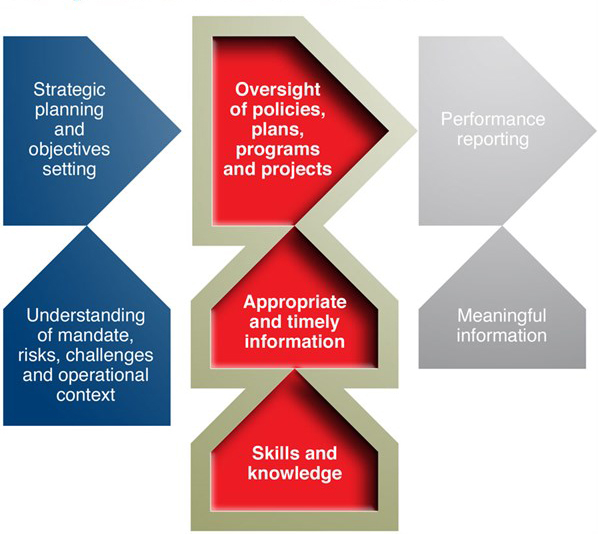
Much has been written about what constitutes good governance, and “good practice” guides have been published in recent years by a number of organizations, including audit offices. (See, for example, the Australian National Audit Office’s 2014 Better Practice Guide Public Sector Governance: Strengthening Performance Through Good Governance.)
While this Practice Guide does not explore all aspects of governance in the public sector, it is useful to highlight the basic principles that support good governance, and therefore oversight, too.
The basic principles of good governance are:
- Accountability
- Leadership
- Integrity
- Stewardship
- Transparency.
These five principles are briefly defined in Figure 2.
Figure 2 – Principles of Good Governance
|
Accountability is the obligation of an individual, a group, or an organization to answer for a responsibility that has been conferred. Leadership is setting the “tone at the top,” which plays a crucial role in encouraging an organization’s personnel to embrace good governance practices. Integrity is acting in a way that is impartial, ethical, and in the public interest. Integrity is reflected in part through compliance with legislation, regulations, and policies, as well as through the instilling of high standards of professionalism at all levels of an organization. Stewardship is the act of looking after resources on behalf of the public and is demonstrated by maintaining or improving an organization’s capacity to serve the public interest over time. Transparency is achieved when decisions and actions are open, meaning that stakeholders, including the public and employees, have access to full, accurate, and clear information on public matters. Source: Modified from Public Sector Governance: A Guide to the Principles of Good Practice, Office of the Auditor General of British Columbia. |
It is also useful for auditors to have a clear understanding of the distinct roles played by both oversight bodies and management. As a general principle, the roles of an oversight body should be segregated from those of management. To illustrate this principle, Table 1 presents the usual roles of boards of directors and management in public sector agencies, boards and authorities.
Oversight bodies are expected to play their respective roles without getting involved in the organization’s day-to-day management. Members of oversight bodies should also be independent from management in order to avoid real or perceived conflicts of interest.
Table 1 – The Separate Roles of Boards of Directors and Management
|
Board’s Roles |
Management’s Roles |
|---|---|
|
|
|
|
|
|
|
|
|
|



